The most actively used Ethereum decentralized app (dApp) 333ETH has just been labelled an “active scam” and blacklisted by popular cryptocurrency wallet MetaMask.

When MetaMask users head to the 333ETH website, their browser will greet them with a message warning them the app could compromise their security.
333ETH – which currently stands as the most popular app on DappRadar – is a smart contract-powered “automated investment distribution” platform that promises daily returns to users.
Sounds too good to be true? Well, it might be. Indeed, Mashable recently compared the platform to a Ponzi scheme.
The 333ETH platform is apparently so ingenious, that after taking some of your initial investment for “marketing,” “technical support,” and “payroll,” users will supposedly immediately begin receiving 3.33 percent daily dividends of the Ethereum sent to its smart contract address.
As schemes with similar promises have taught us , such systems will appear to be functional until the contributions stop coming, after which the whole thing collapses.
So, perhaps in an effort to bring 333ETH to a swift close, the widely popular MetaMask extension will greet users with the following message if they try to reach its website.
333ETH markets itself as providing “security of contributions and life-long payments guaranteed by the Ethereum blockchain.”
There is supposedly added security in knowing that the creators can’t just pull an ‘exit scam’ – and that the Ethereum smart contract system controls all of the funds.
There’s even a referral program (can I get a “ BITCONNEEEEEECCCTTTTT!?! “).
A primary Ethereum use case
It’s a hard truth to stomach, but this is our reality. 333ETH is currently the number one Ethereum dApp in terms of user activity. It currently boasts over 1,700 active contributors, and over the past 30 days more than $3 million in Ethereum has been distributed via its smart contract.
It’s worth noting that 333ETH’s ‘number one’ status has been disputed by MetaMask. When using certain metrics, such as transaction volume or smart contract balance, that’s certainly true.
But when ranked in terms of recent user activity – it is definitely number one. It even rules over decentralized Ethereum asset exchanges IDEX and ForkDelta.
Warning users against obvious Ponzi schemes and other related scams is certainly necessary, especially if the industry has any hopes of achieving the fabled “widespread, global adoption.”
Before that happens, the Ethereum community might have to come to terms with their blockchain being commonly associated with seedy gambling platforms and blatantly dodgy pyramid schemes.
After all – smart contracts are autonomous, and effectively indestructible. Outside of censorship, the only defence we have is education.
If you’re interested in everything blockchain, chances are you’ll love Hard Fork Decentralized. Our blockchain and cryptocurrency event is coming up soon – join us to hear from experts about the industry’s future. Ticket sales are now open, check it out!
Kik raised $98M with a potentially illegal ICO. Now it wants your money to fight the SEC
Kik, the embattled messaging startup behind the Kin cryptocurrency , is now crowd-sourcing donations to help fund its legal battle with US regulators.

The Defend Crypto Fund is said to be tailored specifically to fight the US Securities and Exchange Commission (SEC) “on behalf of the future of crypto in the [United States].”
So far, Kik itself has contributed $5 million to the fund, which is apparently held in special Coinbase accounts. Earlier this month, Coindesk quoted its CEO saying the firm had spent at least $5 million throughout the ordeal already.

“Any additional contributions will be held with Coinbase and will only be used if that $5MM [sic] isn’t enough. In that case, expenses will be disclosed, and — after a court decision is made — the Defend Crypto fund will allocate the remaining resources to other initiatives,” reads an FAQ.
SEC regulators have already commenced legal action against Kik, which raised $98 million in late 2017 with an initial coin offering to develop the Kin blockchain protocol and cryptocurrency ecosystem.
Kin tokens, they say, should have been registered as securities with US regulators. As such, the SEC maintains that Kik‘s ICO violated securities law in America.
Kik‘s entrepreneurial chief executive Ted Livingston thinks otherwise.
In fact, Livingston went so far as to claim that Kin is “the most-used cryptocurrency in the world,” and that over 250,000 people had used it, which (according to Livingston) makes it a currency — not a security.
“For the future of crypto, we all need Kin to win,” reads the Fund’s website. “This case will set a precedent and could serve as the new Howey Test for how cryptocurrencies are regulated in the United States.”
Securities are typically identified through the Howey Test , a framework that (in part) determines whether investors stand to make profit on an investment as a result of the efforts of others.
If investors stand to make money without doing anything at all, it’s likely the asset should be a registered security.
In January this year, footage surfaced that showed Livingston doing his best to hype his Kin token — then in pre-sale ICO phase — by claiming it would one day “become super valuable.”
For more information regarding how the SEC decides which cryptocurrencies are securities, you can read chairman Jay Clayton’s statements on the matter here .
Behind the scenes: Electrum hackers steal $4M with Bitcoin phishing attacks
Electrum Bitcoin wallet users have lost 771 BTC (approximately $4 million) since late December 2018, in an ongoing series of targeted phishing attacks.

According to research released by Malwarebytes Labs, fraudsters were able to trick unsuspecting users into downloading a malicious version of the wallet by exploiting a weakness in the software.
In February , the developers behind Electrum decided to exploit the same flaw in their own software to redirect users to download the latest patched version.
Then, in March , things got worse and developers started exploiting another unknown vulnerability, essentially attacking vulnerable clients to keep them from connecting to bad nodes, which they referred to as a “counter attack.”
After that, a botnet launched distributed denial of service (DDoS) attacks against Electrum servers to better target users with out-of-date, vulnerable wallets.
Why did the attacks happen?
Known as a “lightweight” Bitcoin wallet, Malwarebytes researchers explain Electrum implements a variation of a technique called ‘Simplified Payment Verification’ (SPV).
This technique enables users to send and receive transactions without downloading a full copy of the Bitcoin blockchain (which amounts to hundreds of gigabytes in size).
Instead, Electrum operates in a client/server configuration. The wallet, or client, is programmed by default to connect to a network of peers in order to verify that transactions are valid.
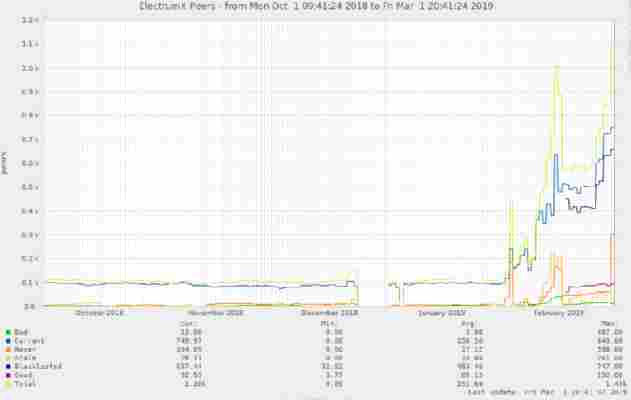
While this has historically been a fairly secure method of transacting, attackers have taken advantage of the fact that anyone is allowed to operate a public Electrum peer.
As the below graph evidences, there has been a significant increase in the number of peers active on the Electrum network:

Malicious wallets
In its findings, Malwarebytes refers to malicious Electrum wallets as “Variant 1,” and “Variant 2.” Research showed the actor(s) behind this specific campaign have been active for some time.
With this in mind, the researchers say it’s plausible that other variations of this malware had been in existence prior to December 21, 2018.
Variants 1 and 2 appear to be operated by different actors, based on several differences found in the malware.
Variant 1 is unique in that the malware authors implemented a function to upload stolen wallet keys and seed data to a remote server. Efforts were also made to make sure this function was hidden by ob fuscating the data exfiltration code inside a file not normally found in Electrum named “ initmodules.py.”
Additionally, any balance found in the wallet was sent to one of the several pre-programmed public addresses controlled by the scammers. In this instance, the selected destination address was dependent on the address format used by the infected users’ Electrum Wallet.
Researchers found that Pay-to-PubkeyHash (P2PKH) addresses were the default method in use during setup, meaning users running default settings appear to be the most hit. This is evidenced by looking at the activity in each of the following addresses:
Variant 2 attacked aggressively, which resulted in it stealing more Bitcoin than Variant 1, the researchers say.
Instead of redirecting victims to a malicious Github site, Variant 2 hosted the malware through a domain that appeared similar to the legitimate Electrum download site.
The findings indicate that the attackers seemingly had a good grasp of Electrum and its code.
For example, they disabled auto-updates, removed prompts for things such as “Yes I am sure”, and even took away the ability to perform Replace-by-fee (RBF) transactions – a function added to the Bitcoin code-base later on in development that would enable the creation of a double spend transaction. In this case, if you were aware about this functionality (and probably few are), you could reverse the stolen funds transfer by double-spending the input using a higher-fee.
So, where have all the coins gone?
By analyzing the transactions on the blockchain, researchers have found that the funds stolen by Variant 1 have been broken down into smaller Bitcoin amounts.
Specifically, 48.36 BTC ($ 244,001) is re-grouped mostly in to 3.5 BTC ($ 17,659) amounts followed by 1.9 BTC ($ 9,586) amounts.
The researchers believe this pattern means it’s likely evidence of a money laundering technique known as “smurfing.”
This is because deposits of $7,000 are less likely to trigger a CTR (currency transaction report) as this amount is under the specified $10,000 threshold.
Future attacks?
Overall, researchers at Malwarebytes ascertain that future attacks are likely.
“Anyone keeping track of cryptocurrencies knows they’re in for a wild ride. Determined threat actors exploited a vulnerability in the most popular Bitcoin wallet to create a very clever phishing attack that was able to net them at least over 3 million dollars in only a few months,” they said in a blog post.
When Electrum responded to protect unsuspecting victims from this theft, the criminals retaliated with sustained DDoS attacks. “ There most likely was some animosity between the two parties, but as the botnet continues to disable legitimate Electrum nodes, rogue ones get promoted to continue the vicious cycle of pushing the fake update and rob more victims of their cryptocurrencies,” continued the researchers.
Ultimately, people running their own Electrum servers can mitigate theses attacks in different ways, but are generally advised to update their wallet to the latest version (3.3.4) from the official repository and asked to remain vigilant in the way of more warning messages disguised as phishing attempts.
Did you know? Hard Fork has its own stage at TNW2019 , our tech conference in Amsterdam. Check it out . eToro will also be making an appearance there!











