Cybersecurity researchers have identified a new strain of Linux malware that not only mines cryptocurrency illicitly, but provides the attackers with universal access to an infected system via a “secret master password.”

TrendMicro’s latest blog also reveals that Skidmap attempts to mask its cryptocurrency mining by faking network traffic and CPU-related statistics.
High CPU usage is considered the primary red flag of illicit cryptocurrency mining, which makes this functionality particularly dangerous.
According to TrendMicro’s researchers, Skidmap demonstrates the “increasing complexity” of recent cryptocurrency-mining threats.
Cryptocurrency mining malware is still a very real threat
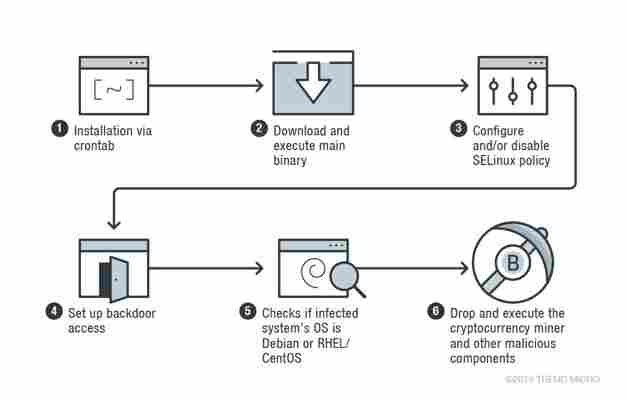
Initial infection occurs in a Linux process called crontab, a standard process that periodically schedules timed jobs in Unix-like systems.
Skidmap then installs multiple malicious binaries, the first minimizing the infected machine’s security settings so that it can begin mining cryptocurrency unhindered.
“Besides the backdoor access, Skidmap also creates another way for its operators to gain access to the machine,” wrote TrendMicro. “The malware replaces the system’s pam_unix.so file (the module responsible for standard Unix authentication) with its own malicious version […].”
“[T] his malicious pam_unix.so file accepts a specific password for any users, thus allowing the attackers to log in as any user in the machine,” added the firm.
Additional binaries are dropped into the system to monitor the cryptocurrency miners as they work to generate digital money for the attackers.

Unfortunately, TrendMicro didn’t indicate which cryptocurrency Skidmap illicitly mines. Hard Fork has reached out to the researchers for more information and will update this piece should they reply.
The firm warned that Skidmap is more difficult to cure compared to other malware, particularly as it uses Linux Kernal Module (LKM) rootkits, which overwrite or modify parts of the OS kernel.
Skidmap is also reportedly programmed to reinfect systems that have been cleaned or restored.
“Cryptocurrency-mining threats don’t just affect a server or workstation’s performance — they could also translate to higher expenses and even disrupt businesses especially if they are used to run mission-critical operations,” wrote TrendMicro.
To protect against Skidmap, TrendMicro urges admins to keep their systems and servers patched and updated, and beware of unverified, third-party repositories.
They should also enforce the “ principle of least privilege ” to prevent malicious binaries from obtaining access to critical system processes in the the first place.
Update 10:38 UTC, September 17: A TrendMicro spokesperson has since contacted Hard Fork to confirm that Skidmap mines Monero, the private-focused altcoin.
“The cryptocurrency miner pertaining to this article is a variant of XMRig which mines Monero cryptocurrency,” they said via email.
XMRig is open-source cryptocurrency mining software available on GitHub.
Cyber criminals steal $27M in Bitcoin by impersonating popular cryptocurrency exchange
Police agencies from the UK and the Netherlands have arrested six people in connection with the theft of €24 million ($27 million) worth of cryptocurrency.

According to a statement , the gang stole Bitcoin from at least 4,000 victims across 12 countries. This is likely just the start, as more are beleived to have been affected; victims continue to come forward.
Following a 14-month long investigation, the group of five men and one woman were arrested at their homes in the south of England, Amsterdam, and Rotterdam, in a coordinated operation yesterday.
Beyond this, details are sparse, but it appears the group was running a website that impersonated a “well-known online cryptocurrency exchange,” Europol said in the statement. The law enforcement agency has not said which exchange, though.
It’s believed the group used “typosquatting,” a technique which uses misspelled URLs, to trick victims into thinking they’re on their desired website, when in fact they’re not.
The website impersonates the genuine site, and when the user attempts to log in, it will forward sensitive user details to the bad actors. These details can then easily be used to drain Bitcoin wallets and exchange accounts.
Another cryptocurrency scam recently used a similar tactic to run a fake token sale. Cyber-baddies impersonated Facebook’s Calibra website , with one minor change to the “i” in the URL. Rather than Calibraom, the scammers use Calìbraom to trick users into thinking they’re on the legitimate site.
Hard Fork has contacted Europol to learn more as the story develops.
Texas regulator goes after cryptocurrency scammers boasting fake Obama endorsements
The Texas State Securities Board (TSSB) is taking emergency action against cryptocurrency scammers, peddling fake endorsements and posing as well-established blockchain services.

In a statement from yesterday, TSSB Commissioner Travis J. Iles revealed the board has issued a cease and desist letter for three cryptocurrency businesses. The suspected businesses are currently under investigation.
The TSSB claims that Coins Miner Investment, DGBK Ltd, and Ultimate Assets LLC have been duping potential customers with incorrect, false, and totally misleading information.
“According to the Emergency Cease and Desist Order, Coins Miner is manipulating its email solicitations to make them appear as if they came from Coinbase,” the statement reads.
DGBK Ltd claims to have developed a “hack-proof device to store and transfer cryptocurrencies.” Oh, and the company is based in Belize. I feel like I’ve read this story before …
This company is also promoting itself by brandishing around social media a 33-second video of Barack Obama supposedly endorsing its products.
Finally, the cease and desist outlines the alleged wrongdoing of Ultimate Assets LLC.
This includes making outlandish claims that investors can turn $1,000 into $10,000 in a matter of three weeks. While the company claims to offer guarantees on initial investments, it is not warning investors that their capital is at risk, and so, is committing fraud.
What’s more, Ultimate Assets appears to be a phantom company, it is not located at the address it states as its headquarters.
This is even more damning considering that a report from New York state’s attorney general has declared that even legitimate cryptocurrency businesses do not offer enough protections for their customers.
These are all good arguments for not trusting anyone in the cryptocurrency market. If you absolutely must place your trust in a person, business, or entity, do your own research and be strict with due diligence.











