Nefarious hackers are wiping files on publicly accessible storage devices and leaving just a Bitcoin ransom note behind.

According to users on the BleepingComputer forums, files on their Lenovo Iomega NAS (network attached storage) devices are allegedly being deleted or hidden. The attackers are demanding Bitcoin in exchange for the safe return of victims’ files.
After the attack, victims are finding their NAS drives empty, except for a text file with the name “YOUR FILES ARE SAFE!!!” One of the ransom notes outlines the attackers’ demand of 0.03 Bitcoin ($280). In this instance, attackers give the victim a deadline of August 1, 2019 to make the payment, or else the files will “be gone for good.”
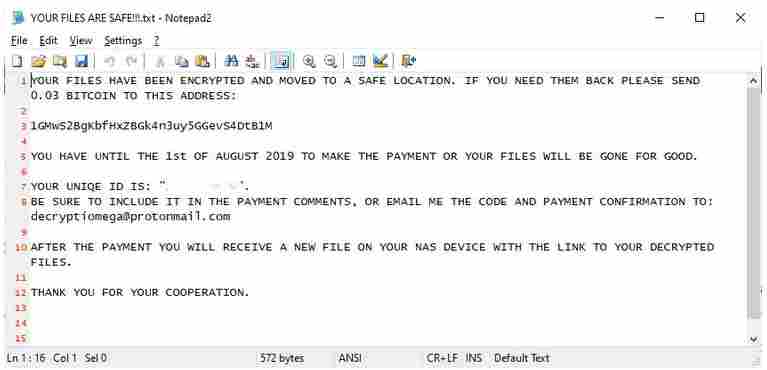

It appears attackers are generating new messages for each victim. That said it’s not immediately clear if it’s the same group of hackers responsible for all the attacks.
Each ransom note appears to list a different Bitcoin address and the amount of Bitcoin hackers demand varies between 0.01 ($100) and 0.05 ($470) Bitcoin.
These are relatively low amounts for data ransom attacks, which have been known to go into six figures . Given that these attacks are most likely on individuals, hackers might be hoping that the low price is enough to lure victims to pay, rather than go through the stress of file recovery themselves.
Sadly, it looks like it might have worked on a few victims.
One of the Bitcoin addresses used in the attack has received nine payments since June 27 which, according to BleepingComputer, could be associated to this campaign. The address has received a total of 0.2 Bitcoin ($1,900).
Initial reports confirm that, unlike typical ransomware attacks, files are being deleted rather than encrypted.
One victim said they managed to use file recovery software to recover their lost files, by attaching his NAS drive directly to their PC.
While it’s not been confirmed how hackers are gaining access to these network drives, BleepingComputer found there are numerous unsecured Iomega NAS drives directly attached to the internet. So it sounds like it might be quite straightforward.
Iomega network storage devices have a publicly accessible front-end, so users can access their files over the internet. This is a great feature if you want to run your own “cloud” on your home network, but if you don’t appropriately secure it, the device will be open for the world to see.
One victim admitted that they hadn’t secured their Iomega NAS drive sufficiently, and suspected this was exploited by hackers in the attack. Largely it seems that users, and not Lenovo, are at fault here for not securing their own devices.
Lenovo issued has previously released an advisory note giving users information about best practices when it comes to securing Iomega NAS drives.
Update, July 31, 2019, 0850UTC: Updated Lenovo advisory note for clarity. A spokesperson from Lenovo said there is no new security flaw. The advisory note is “guidance for users to lock their proverbial door.”
California man laundered $25M through his own DIY Bitcoin ATM and exchange
A man from the small town of Westwood in California has pleaded guilty to running an unlicensed Bitcoin exchange and ATM, and laundering money.

Kunal Kalra, 25 has been found guilty of owning and operating unlicensed money transmitting business which he used to exchange up to $25 million in cash and virtual currencies. Court documents allege the service was used by dark web drug dealers and other criminals.
According to said documents, this is believed to be the first federal criminal case charging an unlicensed money remitting business that used a Bitcoin kiosk.
Kalra – who was also known as “kumar,” “shecklemayne” and “coinman” – ran his business between May 2015 through October 2017 where he exchanged US dollars for Bitcoin and back again. He charged commissions for exchanges and only dealt with high-value clients. Kalra set a minimum exchange value of $5,000 per transaction.
In his plea, Kalra admitted to exchanging Bitcoin for cash on behalf of criminals including those that were selling narcotics on the dark web.
It seems he didn’t care to conduct background checks; that’s likely what got him caught through a number of sting operations.
In 2017, he fell for a sting in which an undercover agent used Kalra’s services to exchange $400,000 cash into Bitcoin. The agent told Kalra the cash came from drug trafficking but that didn’t dissuade the perp from continuing with his criminal scheme.
In June of the same year, Kalra sold nearly two pounds of methamphetamine to another undercover agent for $6,000. The perp then met with the same agent at a later date where they asked to exchange $50,000 in Bitcoin for cash. The agent again said the money came from selling drugs.
If that wasn’t enough, Kalra also admitted to operating a Bitcoin ATM where his customers were exchanging Bitcoin for cash, and vice versa. Customers were charged for the service. Court documents also state that the ATM had no form of know-your-customer (KYC) or anti-money laundering (AML) processes in place.
Authorities have seized nearly $889,000 in cash from the perpetrator, along with 54.3 Bitcoin ($561,000 at press time), and an assortment of other cryptocurrencies.
While Kalra has pleaded guilty and is yet to stand trial for his crimes, the outlook doesn’t look good. The maximum possible sentence for the aforementioned crimes is life in prison.
ICO fraud update: DJ Khaled and Mayweather walk free, Kevin Hart next to be investigated
The US Court for the Southern District of Florida has dismissed the case of initial coin offering (ICO) fraud against DJ Khaled and boxer Floyd Mayweather.

The court decided that despite Khaled and Mayweather shilled defunct cryptocurrency firm CentraTech (and its associated ICO of CTR tokens) on their social media profiles, they did not play a big enough role in its promotion to warrant further legal action.
“The Plaintiff’s complaint fails to establish that Mayweather [and Khaled] ‘successfully solicited’ the Plaintiffs to purchase CTR Tokens,” according to court documents .
Mayweather and Khaled both posted two tweets related to CTR tokens, one of which encouraged their followers to buy into the ICO. However, the courts state this is the closest the pair ever came to soliciting the tokens for sale.
Seen as it was a series of indirect tweets, the courts could not ascertain whether this successfully encouraged followers to buy CTR tokens. What’s more, courts could not determine if their followers had even seen the tweets, or if the pair had any direct contact with purchasers.
In some cases, investors bought CTR before Mayweather and Khalid were even involved in the project.
For Mayweather and Khaled to have been found guilty, the purchasers (plaintiffs) needed to prove a direct relationship with the defendants. Seen as prosecutors couldn’t prove any such relationship, the court has dismissed the case.


Last November, the US Securities and Exchange Commission (SEC) fined Khaled and Mayweather for their failure to disclose the payments they received to promote CentraTech.
At the time, Mayweather agreed to pay $600,000 in penalties, and DJ Khaled ended up paying a $150,000 fine.
One in one out
Indeed, while it might be good news for Mayweather and Khaled on this occasion, it’s not a great week for American comedian Kevin Hart. The world’s second highest paid comedian is being put under the microscope for his role in shilling tokens for the FLiK ICO started by rapper TI .
Last week, investors affected by TI’s failed cryptocurrency amended their complaint to include Hart, who they are accusing of fraud, Decrypt reports .
Investors are claiming to have lost over $1.3 million by purchasing “worthless” FLiK tokens promoted by TI and Hart in a series of tweets.
Given the outcome of the Khaled and Mayweather case though, if all Hart did was post a series of tweets about FLiK, the precedent suggests he won’t be found culpable for investors’ losses.











