Two divisions of the United Nations are joining forces to bring distributed ledger technology (DLT) to Sierra Leone. The project will try to give citizens greater control of financial credit and identification.

At the 73rd UN General Assembly, the organization announced the UN Development Program (UNDP) and the UN Capital Development Fund (UNCDF) have reached agreement with Sierra Leone’s president, Julius Maasda Bio, to modernize the country’s credit system.
Non-profit Kiva, which crowdfunds loans for the less advantaged, will also join the UN project.
“The Government of Sierra Leone has signed a Memorandum of Understanding (MOU) with UNDP, UNCDF and Kiva on strengthening our National Digital Identification and Credit Reference Bureau process,” said President Maada Bio . “ Sierra Leone will now modernize its Credit Reference Bureau and radically transform its financial inclusion landscape.”
Kiva will bring DLT in the form of the Kiva Protocol. The DLT aims to create a national identification system, that gives control of personal credit data to citizens.
Kiva will track everything from bank loans to credit with local shopkeepers, which will allow citizens to build up a credit history over time.
When Kiva knows the credit history of Sierra Leone’s citizens, lending risk can be quantified, and further lines of credit can be appropriately granted.
Let’s not be taken away by the allure of blockchain and DLT. Sierra Leone is one of the world’s poorest countries , it undeniably needs support from the likes of the UN.
When conversations turn to credit and loans, risk is always involved. There is also risk in using blockchain and DLT as they are developing technologies.
Boston Consulting Group found in many cases the blockchain can’t fix everything, sometimes it can even have a negative impact.
For the sake of Sierra Leone, let’s hope this project has a positive outcome. Remember, blockchain is software, not the silver bullet to all of the world’s problems.
If you’re interested in everything blockchain, chances are you’ll love Hard Fork Decentralized. Our blockchain and cryptocurrency event is coming up soon – join us to hear from experts about the industry’s future. Ticket sales are now open, check it out!
Monero slams crypto-jackers after mining malware hits government sites
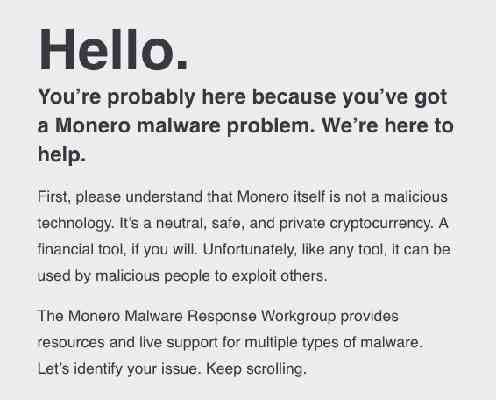
The Monero community has publicly denounced the individuals behind the massive cryptocurrency mining malware campaign, designed to steal users’ computing power to illegitimately bank on XMR.

“The Monero community condemns this malicious, non-consensual use of equipment to mine,” the statement reads. “[…] The Monero community does not want to sit idly by as victims struggle to understand the impact of mining and ransomware.”
It has seen it necessary to establish a “self-organized set of volunteers,” providing tools and resources necessary for protection against crypto-jackers and other malware.
To which extent, the Monero Malware Response Workgroup will be an official, sanctioned resource for protecting oneself against “unwanted in-browser mining, system mining, and ransomware.”

Crypto-jackers love Monero
Crypto-jacking refers to the injecting of malware that forces a machine to mine cryptocurrency. The malware generates digital coins using stolen processing power and sends them directly to the attacker – all without the users’ knowledge.
Most of the cryptocurrency-focused malware infecting the web actually mines Monero (XMR). Specifically, hackers have been known to favor modified versions of the browser-mining script CoinHive , which estimates suggest generates around $250,000 worth of XMR every single month.
Organizations can actually use CoinHive for good – charities are employing it to democratize the donation process to help those in need.
Still, having Monero be the preferential cryptocurrency for the internet’s crypto-jackers is undeniably bad for Monero’s image – which probably gives us the reason for this sudden interest in internet-safety.
This could very well be the first time Monero (or any other blockchain) has officially denounced crypto-jackers.
“It’s our mission to resolve an unfortunate situation as well as possible,” the statement admits. “ We will not be able to eliminate malicious mining, but we hope to provide necessary education for people to better understand Monero, what mining is, and how to remove malware.”
CoinHive is spreading
Research indicates that hackers released 2.5 million new crypto-jacking scripts in the past three months – many of them new CoinHive implementations.
Recent reports suggest that attackers have used them to infect 280,000 MicroTik routers around the world.
MicroTik has since pushed a patch – but it is up to those who maintain the servers to properly clean out their systems. If they don’t, well, the scripts just keep on running.
Over the past week, this has played out in real-time. Security research unit Bad Packets Report detected more than 600 compromised MicroTik running on the network of the main service provider for the Douglas County PUD, a US non-profit utility with close ties to the government.
Hard Fork has since reached out to Douglas County PUD to confirm the security status of its network.
Other international governments have been affected, too. Several Indian municipality websites were recently found to be forcing visitors to mine Monero unawares.
In any case, if you do feel a sudden urge to make sure your machine isn’t generating sweet, sweet, cryptocurrency for someone else – head over to the new Malware Response Workgroup and get yourself checked out. Better to be safe than be the chump.
If you’re interested in everything blockchain, chances are you’ll love Hard Fork Decentralized. Our blockchain and cryptocurrency event is coming up soon – join us to hear from experts about the industry’s future. Ticket sales are now open, check it out!
Man charged with running Bitcoin–powered fake ID cartel gets a year in US prison
A man charged with creating fake IDs in a major Bitcoin -powered distribution ring has been sentenced to one year and one day in US federal prison.

Aaron Kuns, from Toledo (Ohio), who pleaded guilty in June, will also be subject to three years on supervised release and will have to forfeit his cryptocurrency holdings — valued at around $9,675 in April.
Kuns, who had no prior criminal history, told Judge Jeffreey Helmick that he accepted responsibility and apologized for his actions , while maintaining he had made poor decisions after consuming marijuana .
Robert Kern, assistant US attorney, said the IDs created by Kuns were of very high quality , complete with working coded magnetic strips . “Someone could have actually gotten on an airplane,” he said.
Kern highlighted that many of the IDs were bought by adults , who often purchased multiple IDs with different names, and presumably used them for criminal activity .
The fake ID ring first came to light in early 2018, when four individuals (including Kuns) were indicted.
Others charged included Mark Alex Simon, Sarah Alberts, and Benjamin Stalets.
As previously reported by Hard Fork, Alberts pleaded guilty to money laundering and other charges in July. She’s due to be sentenced on October 8.
Simon is also expected to be sentenced in October, while Stalets will find out his fate in December .
Come say hi to the Hard Fork team at our blockchain event . On October 15-17 in Amsterdam, hear from top experts as they discuss the industry’s future.











