Cybersecurity researchers have detailed a dangerous botnet specifically targeting businesses to steal sensitive data and cryptocurrency.

Dubbed “ MasterMana Botnet ,” the ongoing campaign is believed to be connected to the “ Gorgon Group ,” a crew of cyberbaddies linked to worldwide criminal activity and repeated attacks on governments.
“This operation, which began as early as December of 2018, appears financially motivated, given the seemingly indiscriminate targeting of business email addresses via phishing and the inclusion of specific functions to steal information associated with cryptocurrency wallets,” said security firm Prevailion.
“While most companies fear they may become compromised by advanced actors, this particular report highlights that actors do not have to rely on advanced tools or techniques to have a serious business impact,” added the firm, which estimates that roughly 3,300 machines have been infected so far.
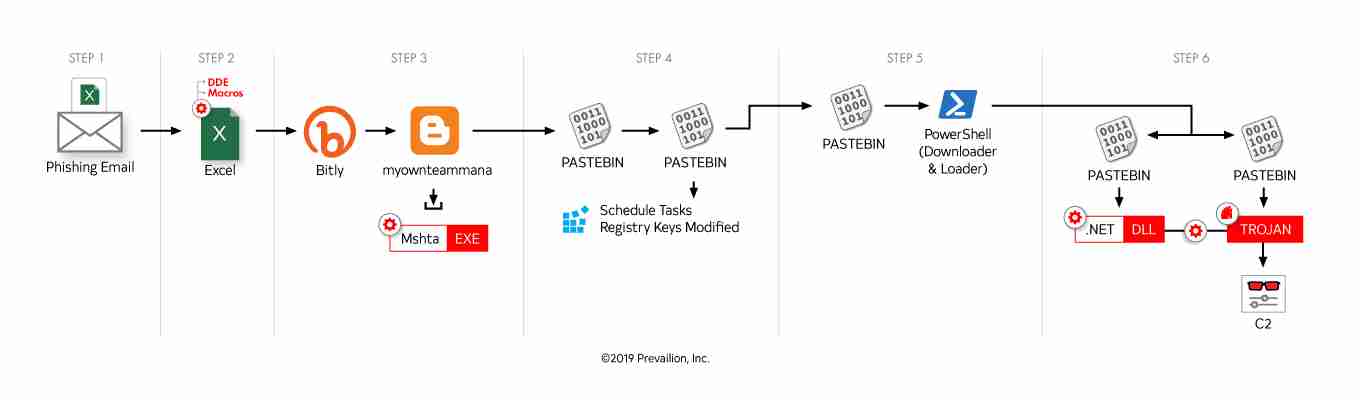

RATs are MasterMana BotNet’s best friend
The campaign operates like this: victims are tricked into opening a phishing email that forces their machine to download a malicious .NET “dll” file. This file assumes system processes before installing a trojan that operates as a backdoor (particularly Revenge Rat or an Azorult variant).
Revenge Rat is a well-known trojan that allows a machine to be remotely accessed, while the Azorult variant analyzed by Prevailion was designed to steal usernames, passwords, web history, cookies, as well as contents of cryptocurrency wallets.
The Azorult variant is even reportedly capable of uploading and downloading files, and even taking screenshots of the victim’s machine. Analysts noted this could lead to the deployment of additional payloads such as cryptocurrency miners and ransomware.
MasterMana Botnet is also noteworthy for the way it evades detection by pulling malicious code hosted by third-party websites such as Blogspot, Bitly, and Pastebin, rather than remote domains controlled by the attackers.
Prevailion also highlighted just how cheap the campaign is to run, as it leverages well-known trojans sold on dark web forums for $100. The only other reported costs were those associated with leasing Virtual Private Servers, which total around $60.
The firm warns that this particular threat actor is likely to continue operating the campaign. “[P]revious public reporting has not deterred them, therefore we wanted to highlight their new modus operandi, so that network defenders may more easily identify their operations.”
Tokyo crypto-cops nab their first cryptocurrency hacker: the $134K Monacoin thief
In Japan, an 18-year-old was charged with stealing $134,000 (¥15 million) worth of cryptocurrency, marking the first time local authorities have succeeded in nabbing a hacker for pilfering digital assets.

The Tokyo police department’s cybercrime division identified its suspect for illegally withdrawing virtual currency from Monappy, a cryptocurrency-infused social media platform, reports JapanTimes .
The man later admitted to repeatedly hacking the Monappy service between August and September last year, which caused it to pay out cryptocurrency illegitimately.
An internal Monappy investigation discovered he had applied for roughly 8,200 “Monacoin” remittances using special “gift codes,” which caused around 640 incorrect transfers to execute.
In total, 97,000 Monacoins are said to have been illegally withdrawn, originally belonging to around 7,700 Monappy customers who had been using the site to store their digital coins.
Those Monacoins are currently worth around $50,000 but at the time, its price was almost double what it is today .
“I felt like I’ve found a trick that no one else knows,” the suspect told local media sources. “I’ve been aware that what I was doing was wrong, but it was fun to see my account balance continue increasing.”
He then reportedly commented that he had committed the crimes as if he were playing a game.
This isn’t the first case of theft-via-hacking in Japan. Back in early 2018, exchange service Coincheck suffered a devastating attack that saw over $500 million in cryptocurrency stolen, which is still the largest attack in cryptocurrency history.
Did you know? Hard Fork has its own stage at TNW2019 , our tech conference in Amsterdam. Check it out .
Hackers hid malware in a fake trading app to steal your cryptocurrency
Security researchers have uncovered a knock-off cryptocurrency trading website designed to steal the funds of unwitting victims.

Cybercriminals have created a website that imitates the Cryptohopper cryptocurrency trading platform to distribute malware that could steal personal information, hijack your clipboard, and crypto-jack your system, Bleeping Computer reports . It appears to have helped hackers amass a trove of over $260,000 in various cryptocurrencies.
When users visit the imitation Cryptohopper website, their system will automatically download and execute a file simply called Setue. While on the surface it might appear legitimate, it’s actually a Trojan.
On execution, the Trojan installs two further viruses: one acts as a cryptocurrency miner, and the other, as a clipboard hijacker. This kind of attack helps hackers earn digital coins from the mining, whilst also potentially stealing passwords, addresses, usernames, and other sensitive information that people might copy to their clipboard.
According to researchers, the malware attempts to steal browser cookies, payment information, login credentials, cryptocurrency wallets, auto fill data, and two-factor authentication data.
The clipboard hijacker component appears to have given the attackers some success already, though.
When a user copies a cryptocurrency wallet address to their clipboard, the hijacker will replace the address with one belonging to a wallet in their control. As such, any funds are directed to the attackers and not to the intended recipient.
That said, researchers are unable to say exactly how much has been earned from this particular campaign on its own, but have identified wallets associated with the attackers which hold a sizable amount of cryptocurrencies.
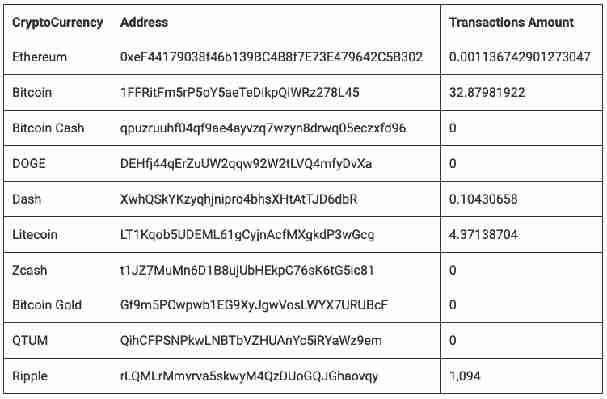

By the looks of things, the attackers have purloined over $260,000 in assorted cryptocurrencies from their exploits. The majority of which has been obtained through redirected Bitcoin payments, earning them over $257,000. How much of this has been earned through hijacking clipboards, is difficult to say.
Hiding cryptocurrency stealing viruses inside seemingly legitimate sources is nothing new sadly.
Last year, malware distributors hid cryptocurrency mining malware in Adobe Flash updates to hide malicious files. Hackers employed a similar tactic where they hid malware in legitimate Windows installation files.
Always be sure you’re updating your system with files from legitimate sources. And in this case, it can’t hurt to double-check cryptocurrency wallet addresses after you paste them from your clipboard.











