Microsoft‘s antivirus and malware division recently opened the bonnet on a malicious mutating cryptocurrency miner. The Washington-based big tech firm revealed how machine learning was crucial in putting a stop to it spreading further.

According to the Microsoft Defender Advanced Threat Protection team, a new malware dubbed Dexphot has been infecting computers since last year, but since June 2019 has been burning out thanks to machine learning.
Dexphot used a number of techniques such as encryption, obfuscation layers, and randomized files names, to disguise itself and hijack legitimate systems. If successful, the malware would run a cryptocurrency miner on the device. What’s more, a re-infection would be triggered if system admins detected it and attempt to uninstall it.
Microsoft says Dexphot always uses a cryptocurrency miner, but doesn’t always use the same one. XMRig and JCE Miner were shown to be used over the course of Microsoft‘s research.
At its peak in June this year, 80,000 machines are believed to have displayed malicious behavior after being infected by Dexphot.
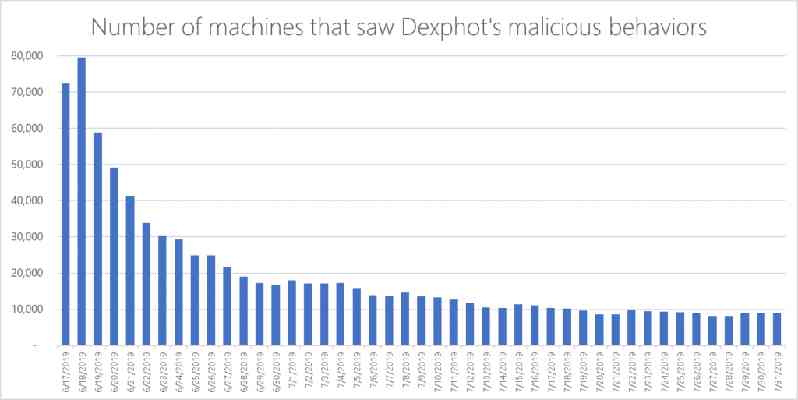

Detecting and protecting against malware like Dexphot is challenging as it is “polymorphic.” This means that the malware can change its identifiable characteristics to sneak past definition-based antivirus software.
While Microsoft claims it was able to prevent infections “in most cases,” it also says its “ behavior-based machine learning models ” acted as a safety net when infections slipped through a system’s primary defenses.
In simple terms, the machine learning model works by analyzing the behavior of a potentially infected system rather than scanning it for known infected files — a safeguard against polymorphic malware. This means systems can be partly protected against unknown threats that use mechanics similar to other known attacks.
On a very basic level, system behaviors like high CPU usage could be a key indicator that a device has been infected. When this is spotted, antivirus software can take appropriate action to curtail the threat.
In the case of Dexphot, Microsoft says its machine learning-based detections blocked malicious system DLL (dynamic link library) files to prevent the attack in its early stages.
Microsoft has not released any information on how much cryptocurrency was earned as a result of the Dexphot campaign. But thanks to Microsoft‘s machine learning strategy it seems to be putting a lid on it, as infections have dropped by over 80 percent.
It seems as long as there is cryptocurrency, bad actors will attempt to get their hands on it.
Just yesterday, Hard Fork reported that the Stantinko botnet, that’s infected 500,000 devices worldwide, has added a cryptocurrency miner to its batch of malicious files.
Intel lost $42B in market value after revealing it might not make its own next-gen chipsets
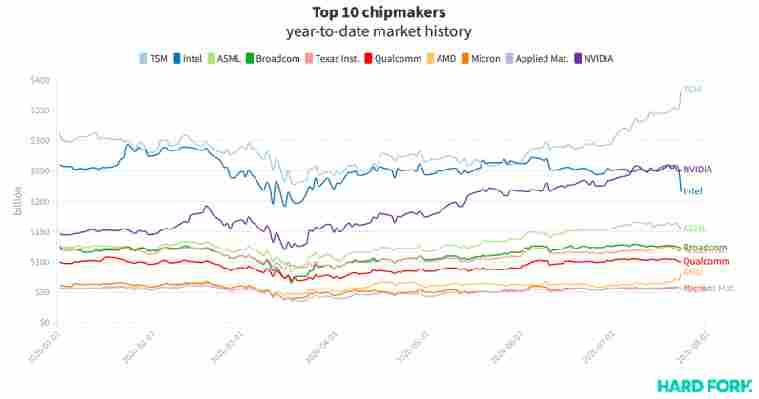
Intel stock plunged on Friday after the US computing giant revealed a third-party manufacturer might make its next generation chipsets — wiping $41.72 billion from its market value.

The announcement sent traders flocking to Intel‘s rivals. Taiwan’s TSMC, the world’s largest chipmaker by market cap, grew by $33.8 billion on Friday, while AMD added $11.5 billion.
According to Bloomberg , TSMC’s 10% rally sent its stock to its highest point since 1990, ranking it the 12th most valuable stock in the world, tech or otherwise. TSMC produces chipsets for AMD, among others.
Remarkably, AMD’s stock surge mirrored Intel‘s losses; $AMD closed the day up 16%, $INTC down 16%.

Wall Street insiders even took turns battering Intel stock as it fell. One analyst reportedly referred to Intel‘s earnings call as the company’s worst over the 45 previous calls they’d covered. Swathes of others either downgraded $INTC or decreased their price targets.
Intel‘s dramatic loss had another effect: it solidified competitor NVIDIA as the US’ most valuable chipmaker, after the Santa Clara firm eclipsed Intel for the first time earlier this month.
In fact, NVIDIA has grown faster any other US-listed chipmaker this year, having added a butt-clenching $104 billion to its market value this year (71% growth).
AMD is currently second with $23.8 billion (41.5%), and TSM is third with $72 billion (23%).
Here’s how law enforcement catches cryptocurrency criminals
When Satoshi Nakamoto first created Bitcoin , they probably had no idea that it would go on to become the dark web’s favorite cryptocurrency — or that it would, in fact, pave the way for other coins that would eventually be used to fulfill other illicit purposes.

The links between cryptocurrency and crime have long been documented. Silk Road ’s infamous collapse after it was shut down by law enforcement in 2013, for example, highlighted how the technology was being exploited by criminals in the hidden corners of the internet.
Criminals use cryptocurrencies such as Bitcoin for various purposes: laundering dirty money , scamming victims out of funds, defrauding investors , monetizing ransomware , or buying illicit goods. For years, reports have also suggested that well-known terrorist organizations such as ISIS or Al-Qaeda were using cryptocurrencies to procure funding .
Hard Fork has covered countless stories about cryptocurrency -fueled crime . We’ve also covered instances where law enforcement has successfully caught the culprits .
From our coverage, we can deduce that law enforcement ’s success in catching the bad actors largely hinges on collaboration with fellow agencies and on using new technology. But sometimes the criminals help investigators by inadvertently doxxing themselves .
Charles Delingpole, the founder of ComplyAdvantage, a company that screens entities and monitors transactions, told Hard Fork: “The most famous mistake made by a cryptocurrency criminal is to de-anonymize oneself. When running Silk Road Ross Ulbricht did this by using aliases that were identifiable and traceable back to his real-world identity.”
Analyzing the blockchain
Unlike cash , which is completely traceless and anonymous, blockchain technology is pseudo-anonymous and behaves like an infinite, immutable, data ledger that houses every single cryptocurrency transaction ever made — but it also lets law enforcement agents trace and follow the money.
The fact that Bitcoin transactions leave a trace is not enough to deter criminals . We know that law enforcers aren’t able to immediately identify the parties involved in a Bitcoin transaction, but they can spot and study patterns in the movement of cryptocurrency to profile and de-anonymize suspects .
“The archetypal cryptocurrency crime is that of theft of cryptocurrency . This began with exchange hacks, as we saw with Mt Gox ,” Delingpole added.
“The biggest crime , however, is the theft of savings from thousands of overly trusting millenials and libertarians who believed that somehow cryptocurrencies were a panacea for the failure of investments or the lack of wage growth elsewhere,” he noted.
Law enforcement agencies aren’t working alone, though. They are in fact actively collaborating with several specialized firms in the space such as ComplyAdvantage and Elliptic.
Based in London , and founded by Tom Robinson in 2013, Elliptic provides blockchain analysis services. In fact, when police in the UK wanted to catch a dark web dealer selling sizeable quantities of MDMA , they contacted the company .
“Our focus is on preventing money laundering rather than tracking down criminals ,” Robinson told Hard Fork , adding: “To achieve this, we provide tools to businesses such as cryptocurrency exchanges and financial institutions, that allow them to screen cryptocurrency transactions for links to criminal activity .”
“By making it harder for criminals to launder their proceeds in cryptocurrency , we help discourage the illicit activity in the first place,” he said.

Elliptic’s tools are based on blockchain monitoring. So, when a bank or an exchange screens a Bitcoin transaction through its software, the company is able to trace it back through the blockchain to see whether the funds originated from wallets associated with criminal activity — for example, a ransomware wallet or a dark web marketplace.
“This means that we have to continually collect data relating to cryptocurrency addresses associated with this illicit activity ,” Robinson noted. To achieve this, Elliptic has a team of data analysts and uses several automated processes .
Of course , this is not as easy as it sounds. “The challenge we face is that not every cryptocurrency exchange uses tools like ours, and so there is always somewhere criminals can cash-out without being caught. The hope is that as anti-money laundering regulations are increasingly implemented, there will be fewer and fewer places that criminals can cash-out and launder their ill-gotten gains.”
ComplyAdvantage, founded in 2014, was born out of the frustration experienced by Delingpole, who previously worked as a money laundering reporting officer and lacked adequate resources to do his job .
“We [ComplyAdvantage] help file suspicious activity reports directly to FINCEN and other regulators around the world. We liaise closely with regulators to understand the latest patterns of criminal behavior and then ensure that our clients can then detect and prevent those typologies,” Delingpole told Hard Fork.
Similarly to Robinson, Delingpole was also open about the ever-growing challenges companies are facing in terms of preventing cryptocurrency crime and catching the criminals .
A new way of investigating
If you’ve been involved in Bitcoin for some time, you would have undoubtedly heard about Katherine Haun, the Department of Justice prosecutor-cum-cryptocurrency investor.
She might be best known as the first female general partner to join prominent VC firm Andreessen Horowitz and co-head of its $350 million cryptocurrency fund, but for years, Haun cut her teeth investigating prison gangs, corrupt officials, and the mafia .
However, approximately seven years ago, her career was sent in a new direction after a colleague at the DOJ asked her to look into a mysterious cryptocurrency .
“They said ‘we have this perfect assignment for you’ — there’s this thing called Bitcoin and we need to investigate it,” she told CNBC . “That was the first time I’d ever heard of Bitcoin .”
Interestingly, Haun said she thought of the cryptocurrency in the same way that she perceives cash : an enabler for criminal activity but by no means responsible.
“The government was able to use that same [blockchain] technology to actually track down criminal activity it might not otherwise have been able to,” she said. “Without the technology underlying Bitcoin , we never would have been able to catch those people .”
Her most extensive case to date saw Haun investigate white-collar crime and public corruption, where government agents were exploiting early adopters of cryptocurrency . One of the agents swindled approximately 20,000 BTC — which is now worth some $150 million — while another extorted Silk Road ’s creator, and stole from other cryptocurrency investors.
Had that crime been committed in cash , Haun told CNBC , it would have been nearly impossible to track these people down.
Acknowledging the threat
The US Federal Bureau of Investigation ( FBI ), who owns the world’s biggest Bitcoin wallet , is no stranger to cryptocurrency crime.
Just recently, Christopher Wray, the agency ’s director, said cryptocurrencies were “a significant problem that will get bigger and bigger.” In June last year, the Bureau said it had 130 active cryptocurrency investigations .
Then, in July, US President Donald Trump signed an executive order creating a task force that would in part focus on developing cryptocurrency fraud investigations.
The European Union Agency for Law Enforcement Cooperation (EUROPOL) is also working to keep cryptocurrency criminals at bay.
In fact, in early May, the agency supported Spain in dismantling a criminal organization providing large-scale crypto money laundering services to other criminal gangs.
A few weeks after that, the agency — alongside several other forces — clamped down on cryptocurrency mixing service Bestmixer.io.
Then, in June, more than 300 cryptocurrency experts from both law enforcement and the private sector attended the sixth Cryptocurrency Conference hosted at Europol’s headquarters in The Hague, Netherlands .
During the same month, Europol also declared its intentions to help authorities with the announcement of what it’s calling the “ cryptocurrency -tracing serious game .”
“But that does not mean that innovation has stalled – behind the scenes, the structural requirements for scale and mass adoption are being iterated upon. In order to mass adoption to occur, there needs to be more day to day adoption of cryptocurrencies by average users ,” the entrepreneur continued.
“Cryptocurrency crime with this innovation and broader adoption, therefore, looks a lot like it does today: a mix of theft , blackmail ransoms , and laundering, albeit at a much larger scale ,” he concluded.
Law enforcement is right to acknowledge the criminal threat posed by cryptocurrencies , and while the landscape is not necessarily set to change much, they will have to change and adapt if they’re to continue catching bad actors who will undoubtedly continue to exploit a technology that fulfills their objectives to near perfection.
Cash may still be king, but if criminals want to operate online , cryptocurrencies are their financial weapons of choice.











